Summary
Call tracing is the single most effective tool used to reduce illegal robocalls. By locating the source of an illegal call, illegal activity can be stopped at its source. Further, the fear of discovery by bad actors leads to deterrence, stopping illegal activity before it occurs.
Call tracing has been done by phone companies for the past 100 years—at least since there have been more than two phone companies. This article explains how call tracing usually works today.
Analysis
If two subscribers on the same phone company’s network call each other, the call can be carried and delivered across a single phone company’s network. If a subscriber on one network calls a subscriber on another network, the call must necessarily be handled off between phone companies. Since every phone company in the world does not connect with every other phone company, long distance and international calls much necessarily pass through many different phone companies.
The below illustration shows how a robocall might transition between five phone service providers.
Some phone companies provide local and wireless service to end users and rely on other phone companies to carry calls between networks. Other phone companies provide local service and “wholesale” or “transit” service. Other phone companies provide only wholesale service.
Twenty years ago, a call from Los Angeles to New York would pass through the phone companies that owned the cables or microwave transmitters in between Los Angeles and New York. Today, most wholesale voice service is provided using Voice over Internet Protocol (VoIP). Since VoIP uses the internet to transit voice calls as data packets, wholesale voice telephone service is essentially “virtualized.” A call between India and the United States could literally pass through any country on Earth.
With VoIP, the route that a call takes is not dictated by geography—it is mostly dictated by cost. A criminal call center outside the United States may use multiple different VoIP providers to originate calls. Each of these VoIP providers will use multiple other VoIP providers to transit calls—as will every other provider in the chain between origination and termination. The exact route a call takes is determined by the prices offered from hour to hour by each provider in the chain a call travels through. This is known as Least Cost Routing (LCR).
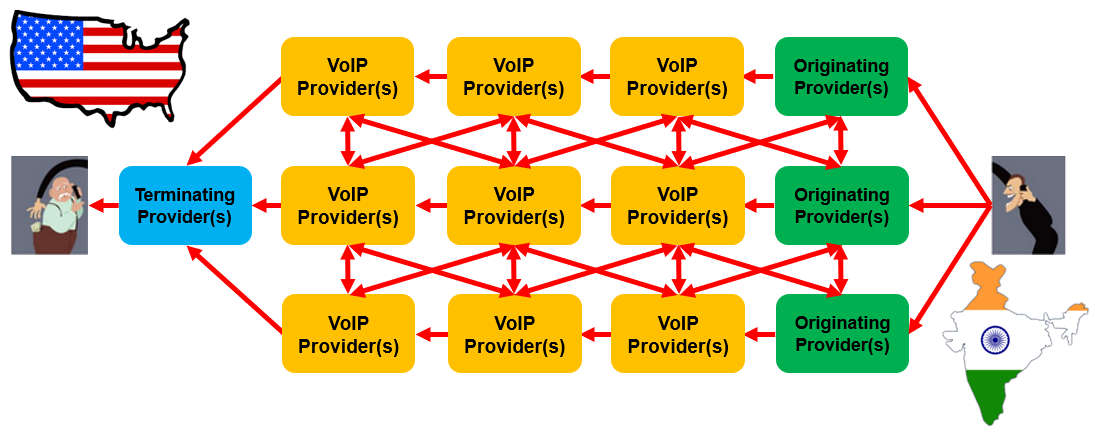
As of October 2023, there are 8,010 voice service providers registered with the FCC’s Robocall Mitigation Database. There are thousands more providers overseas not registered in the US. There are therefore literally millions of routes that a voice call could take in between a foreign country and the US. While the above illustration shows the path of a single call, the actual LCR ecosystem used by an overseas criminal robocalling group looks more like the illustration below.
Without going into technical details about how VoIP works, the VoIP protocol does not use the caller ID number to deliver a call. Someone making a call can therefore enter any value they want into the caller ID field of the outgoing VoIP data packet header. This is easily accomplished using most VoIP dialing software.
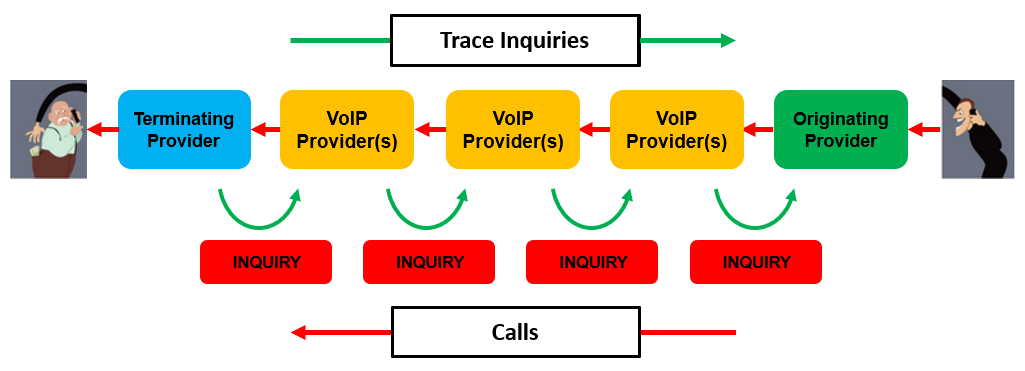
Traceback involves nothing more complicated than a recipient of a call checking to see which phone company sent the call, e-mailing that phone company and asking which came from, and then e-mailing each phone company in the chain until the source of the call is found.
The below illustration shows the direction a call takes “downstream” from its source in red and the direction trace inquires take “upstream” to a call’s source in green.
Phone companies have been doing this for 100 years in order to protect themselves, their customers, and other phone from fraud. Since 1997, such requests for information have been made without legal demands pursuant to the “rights or property” exceptions to telephone record confidentiality found in the Telecommunications Act (the amended Common Carrier Act): 47 USC 222(d)(2).
Such rights or property exceptions are also found in the Stored Communications Act, the Wiretap Act, and the Telephone Records Privacy Protection Act. There is extensive case law allowing for the admission of evidence obtained without legal demand under the rights or property exceptions. This case law also places restrictions on the use of the rights or property exceptions: information cannot be requested while a phone company is acting as an agent of law enforcement. Information disclosed without a legal demand under the rights or property exceptions must be reasonable, necessary, and have a nexus to protecting a phone company’s rights or property.
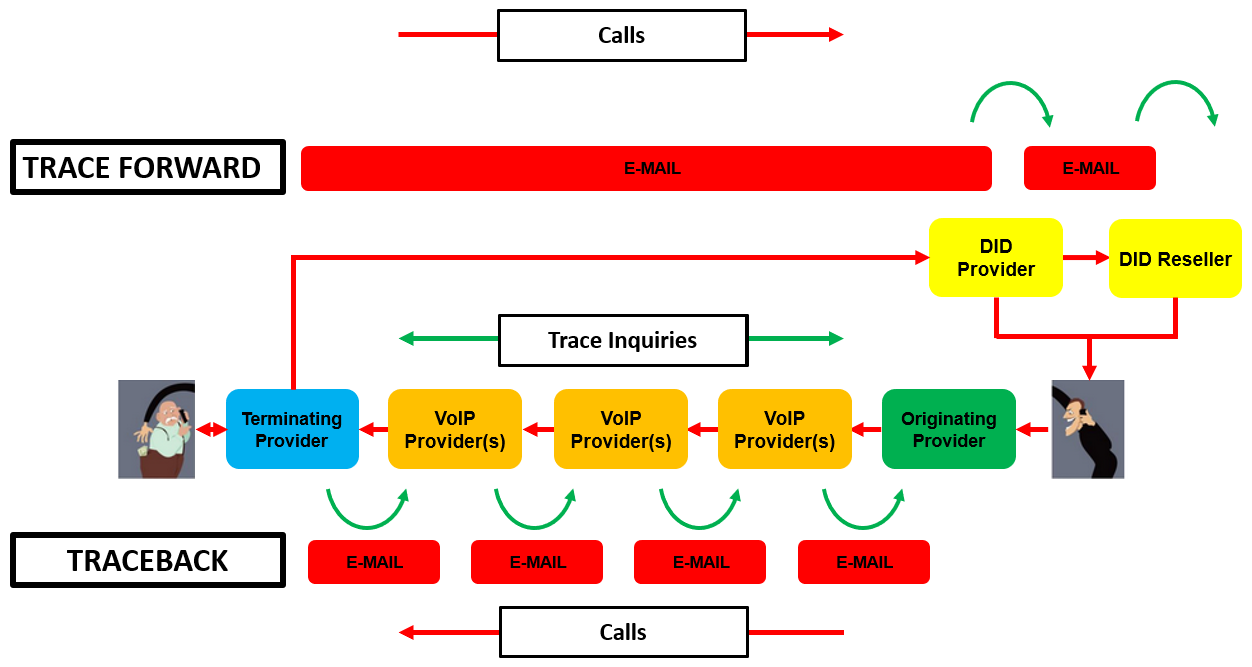
Traceback is not the only way to locate the source of a criminal call center. Outbound spoofed calls are not the only way for criminals to reach potential victims. In fact, between 2015 and 2017 and after 2021 outbound spoofed calls are not the primary ways for scammers to reach potential victims. Criminals also make use of VoIP Direct Inward Dial (DID) numbers so that potential victims can call them back.
Criminals actually prefer the use of DID numbers to outbound spoofed calls because they allow potential victims to “self-select” by calling criminals back. Criminals can disputed call back numbers through computer pop up ads, e-mail messages, and lower volumes of outbound calls. Scammers were forced to primarily use outbound spoofed calls between 2017 and 2021 due to industry and government efforts to quickly disconnect DID numbers used for fraud.
Tracing the use of DID numbers is actually easier than tracing outbound spoofed calls. If a someone wants to receive incoming calls, they must be a subscriber to the number being called.
Whereas an inbound spoofed call from an overseas criminal call center may pass through 4-7 different phone companies in between the points of origination and termination, a call from a victim to a scammer will only pass through 2-3 phone companies.
Tracing “forward” to find the owner of a DID number involves inquiring with the owner of the DID number range and any resellers in the chain between the number range owner and the end user of the DID.
There are other trace methods that are more efficient than e-mailing all providers that handled a call. However, other methods do not work for all types of calls. Details of alternate tracing methods are not detailed here in order to preserve the secrecy of certain investigative techniques.