Summary and Background
Complaints filed with the FTC show scams initiated by text message are a major source of consumer fraud.
A small number of criminal organizations are responsible for the large majority of text message spam complaints. As such, targeted enforcement using specialized investigative techniques can significantly reduce robotexting.
Analysis
There are four methods used to deliver robotexts:
- Prepaid SIM cards used in SIM Boxes;
- E-Mail-to-text message gateways;
- Application-to-Person (A2P) providers; and
- Caller ID spoofing.
The large majority of robotexts are delivered through SIM boxes or e-mail-to-text. Fraudulent A2P accounts are usually quickly shut off by service providers. Caller ID spoofing with text messages is technically feasible, but much more difficult than voice caller ID spoofing.
US wireless providers have robust, sophisticated spam detection, filtering, and blocking tools. As such, the large majority of robotexting, by volume, comes from a small number of persistent, technologically competent criminal groups. The exact proportion of robotexts by delivery method, wireless provider, and criminal group varies widely from month-to-month as criminal groups change delivery methods and wireless providers respond with new blocking measures.
Anyone who receives a suspected robotext can forward the message to 7726 (SPAM) on their wireless phone. US wireless providers keep detailed intelligence about robotexts though analysis of 7726 complaints received from customers. Wireless providers can analyze suspected spam message content, hyperlinks contained in messages, IP addresses registered to links in messages, and originating numbers or e-mail address used to send robotexts.
Law enforcement agencies can identify sources of fraudulent robotexts by obtaining 7726 data though appropriate legal process.
A significant portion of robotexts originate from e-mail-to-text message gateways. Criminals set up large numbers of free e-mail accounts using automated scripts. They then blast as many e-mail messages to wireless phone numbers as they can before e-mail providers shut the accounts down. Wireless providers can monitor, throttle, and block originating e-mail addresses that send too many messages. Criminals therefore need large volumes of free e-mail accounts to operate.
Free e-mail providers have taken significant steps to reduce the bulk activation of accounts using scrips. (Though these measures also impact legitimate free e-mail users.) In addition, the FCC has issued a Notice of Proposed Rulemaking to, “Encourage providers to make email-to-text, a major source of illegal texts, a service that consumers proactively opt into.” (Combatting Illegal Text Messages Second Report and Order and Second Further Notice of Proposed Rulemaking in CG Docket Nos. 02-278 and 21-402, and Waiver Order in CG Docket No. 17-59)
Law enforcement can obtain important information about robotexts from free e-mail service providers through appropriate legal process, including:
- IP addresses used to send messages;
- IP addresses used to register accounts;
- Phone numbers used to register accounts; and
- Device information if accounts were registered using Android or Apple OS emulators.
A significant portion of robotexts originate from prepaid wireless cell phone accounts. These accounts are set up in bulk because wireless carriers typically disconnect prepaid accounts that send text message spam the same day they are used. Criminal groups that deliver robotexts must have a high degree of technical competency in order to circumvent wireless providers’ anti-spam systems.
- Most prepaid accounts used for spam are activated online using numerous proxy IP addresses.
- Given the volume of accounts needed, activation occurs through automated scripts.
- Physical SIM cards must be obtained in large quantities from many different sources.
- Payment must be made through third-parties to avoid detection.
- Messages are sent through SIM boxes and SIM gateway equipment.
A SIM card (or Subscriber Identity Module) is an encrypted thumbnail sized computer chip that provides encoded authorization for a wireless device to access a wireless network. An IMSI (or International Mobile Subscriber Identifier) is a fifteen-digit number assigned to a SIM card. An IMEI (or International Mobile Equipment Identifier) is a fifteen-digit number assigned to a wireless.
“SIM box,” “SIM server,” and “SIM farm” are terms that refer to devices where multiple cell phone SIM cards can be attached in order to make phone calls or send messages. A SIM gateway is a small electronic circuit board (usually two inches square) that functions as a cell phone. Multiple SIM gateways can be connected to a SIM server (or “gateway rack”) so that many different wireless subscribers can transmit from the same location.
SIM cards and antennas can be attached directly to SIM gateways; all three components can be attached to the same server; or antennas, servers with SIM cards, and servers with SIM gateways can be connected together. However, in most cases, SIM card and SIM gateways are kept in different physical locations and connected together through the internet. This way, a physical SIM card in one location can connect to wireless networks and send messages through any number of SIM gateways located anywhere in the world. Complex SIM box networks can involve servers with thousands of SIM cards sending messages from hundreds of SIM gateways in dozens of locations in different States or countries.
Robotexts are easier for phone companies to detect and block than robocalls. This is because the content of a voice robocall is not created until a call is already connected and people start talking. On the other hand, the content of a text message is transmitted as a data package. Phone companies can therefore use some of the data in a text message for filtering and blocking. All major US phone companies deploy robust, sophisticated spam message filtering and detection systems.
This turns defense against robotexting into a game of robot v. robot where robotexters attempt to transmit as many messages as possible before phone companies block them. Robotexters then have to change message content and patterns of delivery. Robotexters use multiple API systems to automate bulk text message delivery, including:
- Activation of bulk freemail accounts (Gmail, Outlook);
- Activation of bulk prepaid SIM cards;
- Third party payment for prepaid SIM cards to avoid detection;
- Delivery of messages via SIM gateway and SIM server devices; and
- Bulk creation of duplicate websites.
THIS SECTION HAS BEEN REDACTED FOR SECURITY PURPOSES.
If you are a law enforcement officer in need of support, please contact FVRO directly.
Additional Investigative Measures for Robotexting
THIS SECTION HAS BEEN REDACTED FOR SECURITY PURPOSES.
If you are a law enforcement officer in need of support, please contact FVRO directly.
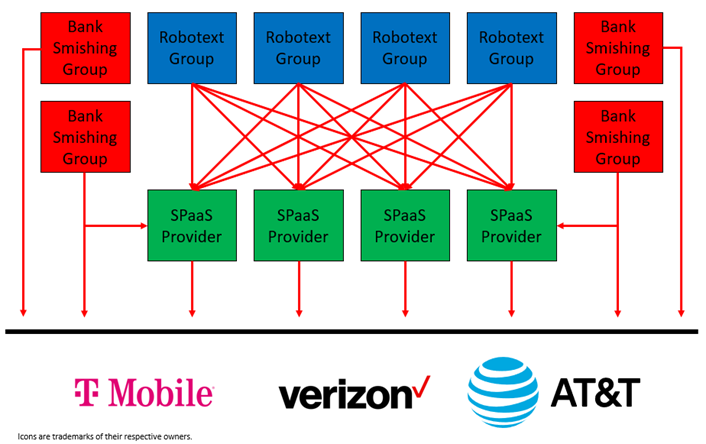
Spam-as-a-Service (SPaaS)
Most robotexts are sent by a small number of Spam-as-a-Service (SPaaS) providers. Multiple spammers and criminal groups crafting scam robotext messages can use the same SPaaS provider. Robotexting groups can also use multiple SPaaS providers. Traditional bank phishing/SMishing messages are sometimes sent through SPaaS providers; but, more often, bank phishing groups are vertically organized and send their own messages.
Unlike other countries, the US does not prohibit any use of SIM gateway devices. However, all US wireless providers prohibit fraud or abuse as part of their terms and conditions of use. They likewise prohibit reselling of services, commercial mass marketing, and the use of automated equipment for commercial purposes without prior authorization.
Wireless carriers can effectively enforce these conditions of use by blocking individual SIM gateway devices. When the IMEI assigned to a SIM gateway is blocked from a particular network, it cannot be used on that network with any SIM card. This is why robotexters spoof different false IMEIs for each prepaid SIM. The spoofed IMEI can be blocked, but the same SIM gateway can still use a different spoofed IMEI.
Modification of a telecommunications device or signal in order to obtain unauthorized use of telecommunications service is a criminal violation of the Federal Access Device Fraud statute (18 USC 1029(a)(7) and (9)).
There are believed to be a limited number of large-scale robotexting groups. As such, the basic outlines of many robotexts follow a common pattern.
- Robotexts are usually delivered using Multimedia Messaging Service (MMS), as opposed to Short Message Service (SMS). This is to conceal message content inside images.
- Multiparty messaging is used to maximize the number of recipients as quickly as possible before e-mail accounts or prepaid SIM cards are shut off by service providers.
- Scams are usually delivered via web links embedded in the message content. Occasionally, potential victims are provided with a phone number to call; but scams are usually delivered via a website.
- Websites are set up in bulk though automated APIs (Application Programming Interfaces) as quickly as possible because they are taken down by service providers.
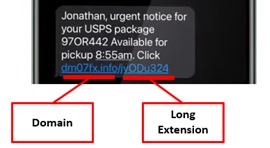
- Web links have long random extensions so that many duplicate websites can be set up, to avoid content filtering by phone companies, and to track which recipients click on messages
- Since robotexters set up numerous duplicate websites, IP addresses tend to be sequential or semi-sequential. Ali Baba and Namecheap are the most comment hosting providers.
- Robotexts are delivered to mobile devices. To defeat attempts to investigate scam websites, readers will be redirected to a legitimate website if a non-mobile device is detected.
The initial landing page website will usually be blank. Readers will be automatically redirected to a series of websites before being presented with a scam. This is so different entities in the chain of websites can say they only paid for traffic to their website and had no idea web traffic had been generated by robotexts.
As reported instances of spam text messages, scam text messages, and “robotexting” have increased over the past several years, many news outlets have treated robotexting and robocalling as similar, interchangeable scams coming from the same criminals. In fact, robocall and robotext scams are completely different. They use different technologies to deliver messages, they are done by different people, they originate from different locations, and they use different methods to extract money from victims.
See the FVRO White Paper: Robocalling v. Robotexting.
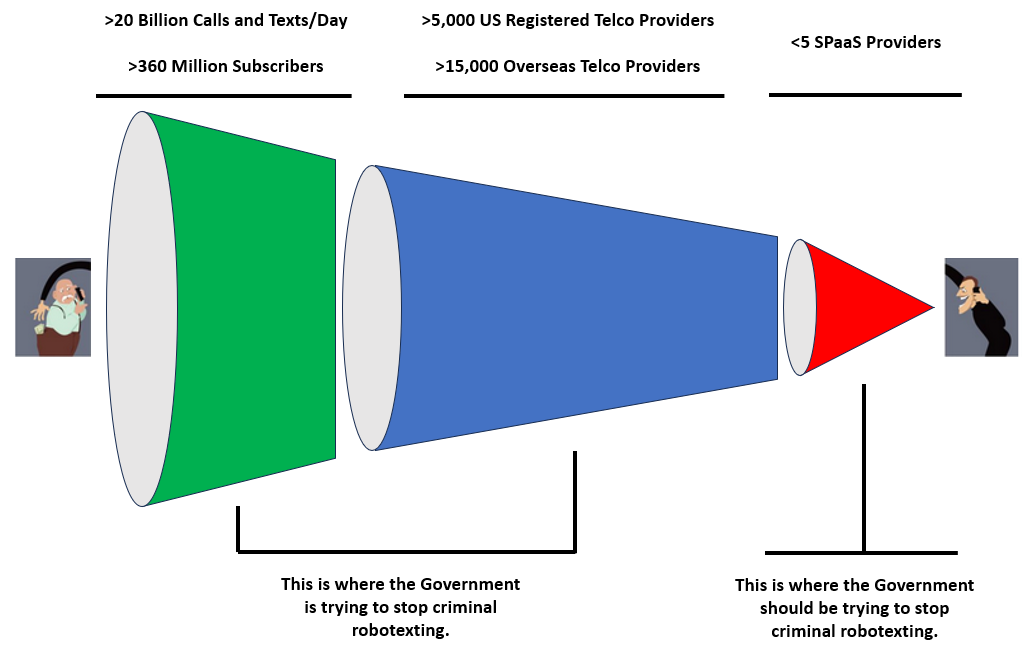
Implications for Policy Makers
The most efficient method of reducing robotexting is to identify, arrest, and prosecute SPaaS provides. Information from such investigations can then be used to pursue major robotexting and SMishing rings.
APPENDIX
By message volume, the most common type of scam robotexts are deceptive offers that result in fraudulent reoccurring credit card charges. This type of fraud therefore warrants additional description.
When a robotext is delivered, it includes a link to a website. Large numbers of websites with random extensions need to be created to avoid detection and blocking by phone companies and also because websites are quickly taken down based on complaints.
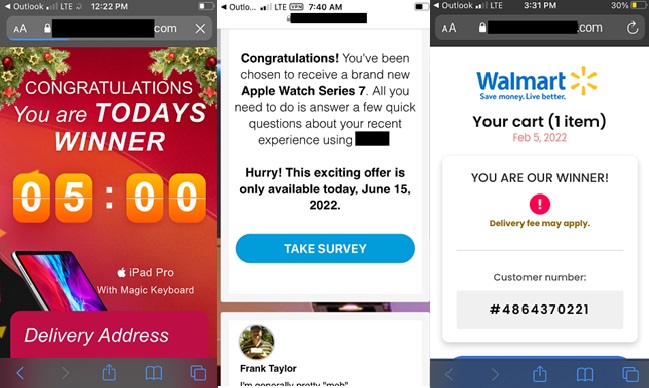
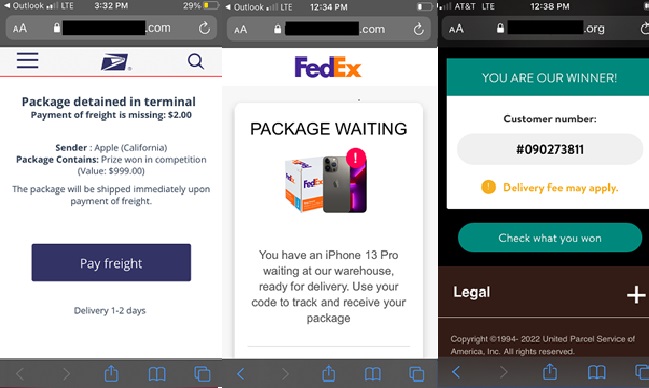
If a reader clicks on the link in a message, they are taken to a blank landing page. This initial website then redirects readers to a series of several websites. This is done so the website collecting money has plausible deniability that the web visitor was responding to a deceptive advertisement delivered by robotext. Once a reader arrives at a scam website, the most common scam is a free prize.
Missed delivery scam robotexts are frequently reported as SMishing; but they are frequently “free prize” offers.
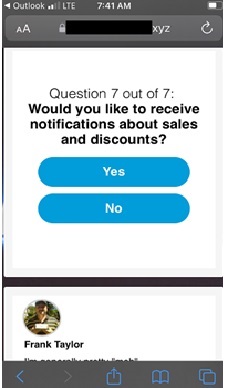
As the reader progresses through a series of scam web pages, they are asked nominal survey questions. Sometimes these survey questions conceal a TCPA consent farm.
As the reader progresses through scam web pages, the branding and messaging of the original robotext are no longer referenced.
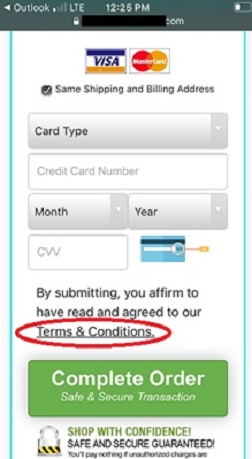
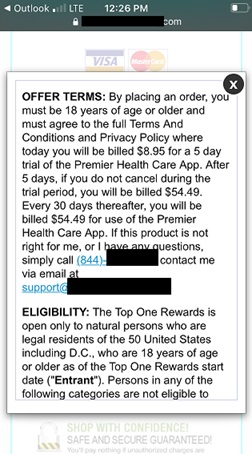
Finally, the reader is presented with a payment request for shipping and handling for their “free” prize.
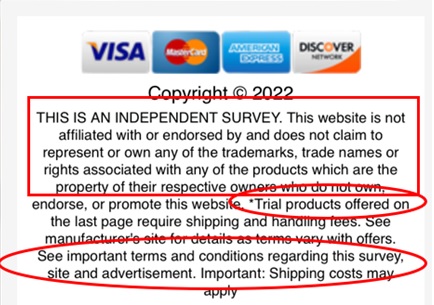
If the reader clicks on “terms and conditions” they will find their prize is not “free” at all. It is a “trial offer.” If they do not return the “prize” within a certain amount of time, they will experience reoccurring charges on the credit card they used to pay for shipping and handling.
This bait-and-switch slight of hand is accomplished by sending readers through many different websites controlled by different parties so that the party collecting payment can claim ignorance about the initial robotext and deceptive offer that sent the reader to their website in the first place.
(Note that the above images are from several different robotexting campaigns and are meant to be representative.)