Summary
Since 2021, criminal groups in India have shifted from making outbound law enforcement impersonation phone calls to distributing call back phone numbers to potential tech support fraud victims via computer pop-up ads and e-mail messages. As a result, tech support fraud has since doubled to become the third most costly type of consumer fraud.
This shift in tactics, however, exposes the locations of criminal call centers to law enforcement. It is easy to trace calls made by potential victims to phone numbers used for scams. A very small group of investigators with proper technical tools and legal demand authority can identify any criminal call center engaged in tech support fraud in near real-time.
Analysis
In July 2021, the FCC required all voice service providers to register with the Robocall Mitigation Database (RMD). Meanwhile, traceback requests made criminal groups aware of industry efforts to locate the sources of fraudulent robocalls. As a result, criminal groups in India shifted from outbound impersonation calls to distributing call back numbers via computer pop-ups and e-mail messages due to the perception that fraudulent outbound robocalls were being more closely monitored and more likely to be traced.
This shift in fraud tactics caused robocalling complaints to the FTC to decline 58% (Q2 2021 over Q3 2024) while dollar loss reported to the FTC from scams initiated by phone call increased 32% during the same period.
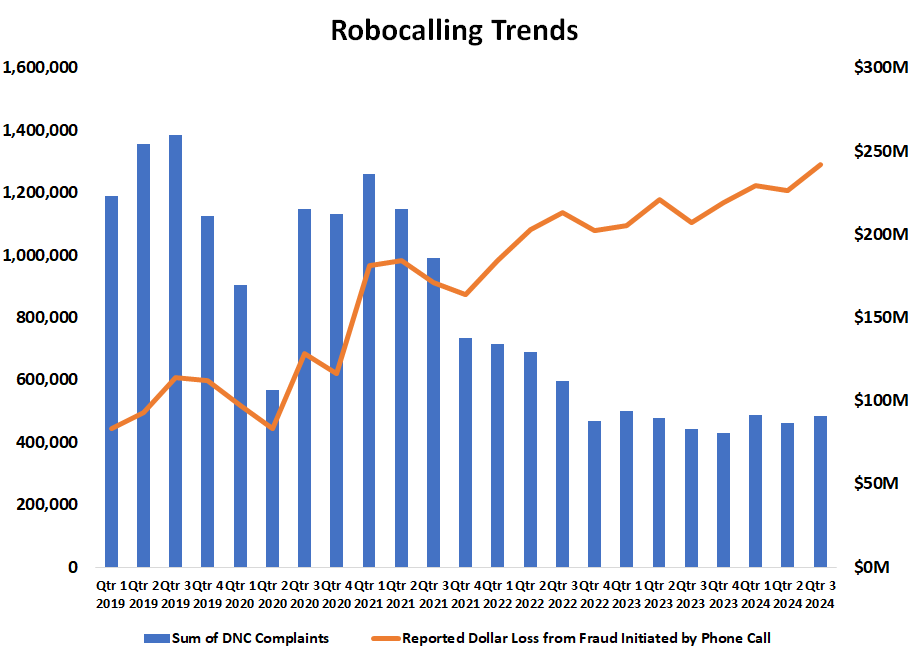
Source: FTC.gov
Some criminal groups have also shifted to using distributed call back numbers for law enforcement impersonation. Other criminal groups in India combine law enforcement and tech support impersonation schemes. The result has been an increase in reported dollar losses attributed to both tech support and law enforcement impersonation while overall complaints about unwanted phone calls have decreased.
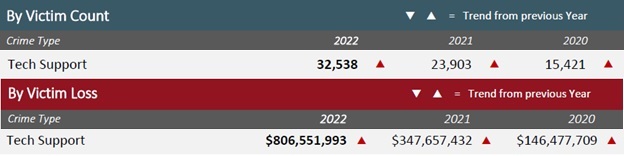
The FBI’s 2022 Internet Crime Complaint Center (IC3) annual report describes this problem and possible investigative opportunities:

The important takeaway for policy makers here is that the use of call back numbers makes it much easier for Indian and US law enforcement to identify and target criminal groups in near real time.
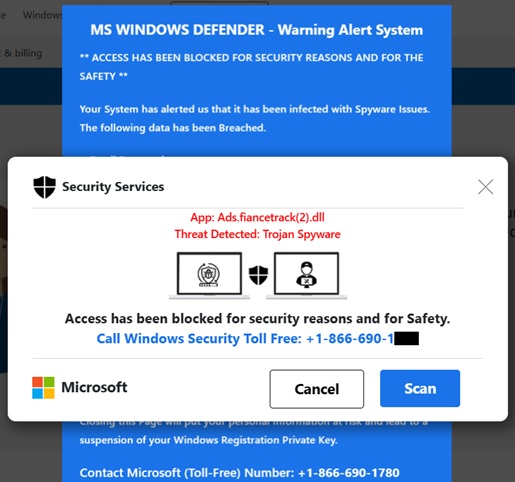
Tech support fraud computer pop-up ads are designed to open a new window and switch to browser full screen mode so that they appear to be operating system alerts, instead of just websites. An example is shown below.
When potential victims call the phone number listed on the pop-up, they are routed to a criminal in India who will attempt to defraud them using various scams.
Criminal groups in India also distribute call back numbers through law enforcement impersonation e-mail messages. An example is shown below.
The goal of providing a call back number instead of making large volumes of outbound calls is to avoid detection by phone companies and to allow potential victims to self-select by calling back.
When a criminal makes an outbound phone call, they can easily spoof the caller ID number. When a phone company receives a spoofed call from another phone company, there is no way of knowing where the call came from. A phone call from India to the United States will pass through 4-7 different phone companies. In order to trace a spoofed call, the phone company receiving the call has to identity and contact each of the phone companies that handled the call. This is known as “traceback.”
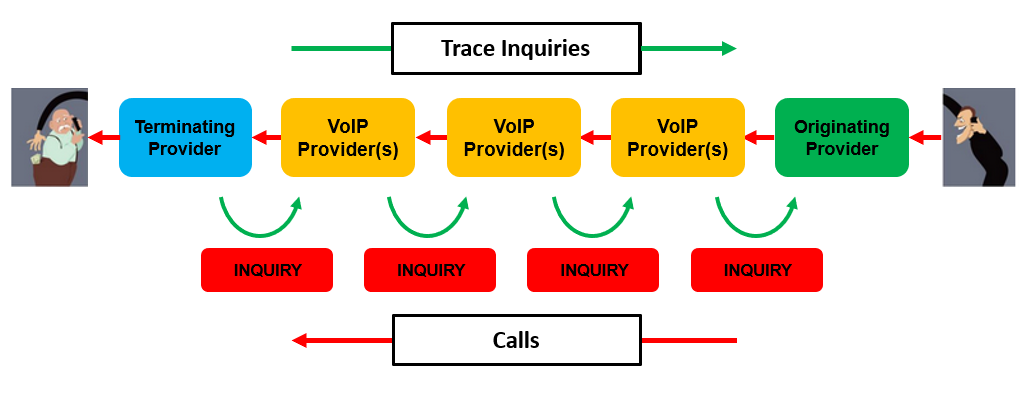
However, when a criminal wants to receive a call from a potential victim, the criminal must be the legitimate subscriber of the phone number being called. This is because phone companies can only send a call to the owner of a phone number range.
To trace who owns a phone number, an investigator need only contact the phone company that owns the phone number and any other phone companies that may have resold use of the number. This is known as “trace forward.”
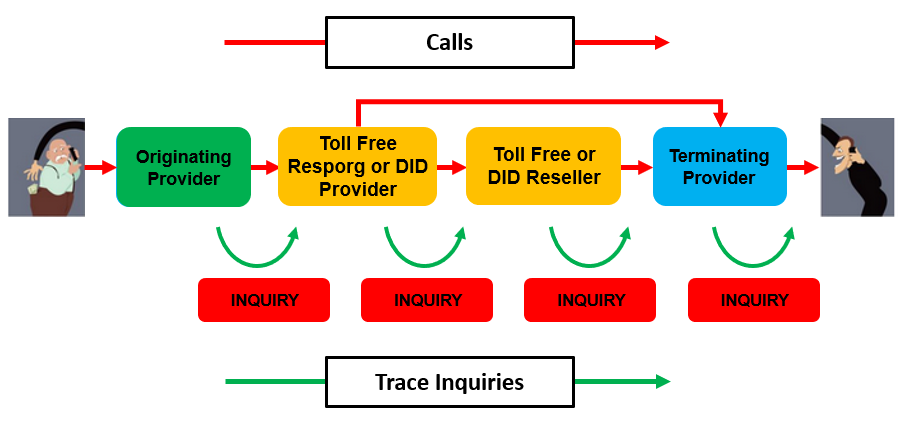
The owners of toll-free phone numbers are known as “responsible organizations” or “Resporgs.” The identities of FCC regulated RespOrgs are publicly available through Somos, the FCC’s designated number administrator : https://www.somos.com/find-toll-free-number.
In many cases, criminal groups will use a non-toll-free number—usually beginning with 8 in order to look like a toll-free number. These virtual call back numbers are known as Voice over IP (VoIP) Direct Inward Dial (DID) numbers. As with toll-free numbers, the owner of a DID number can be identified by the number range through publicly available websites and by inquiring with any entities that resold a number.
Once the end user of a call back number is identified, the phone company providing service to the criminal end user will have a record of the IP address used to receive calls. Indian police can then locate criminals receiving calls by inquiring with Indian internet service providers.
It is always easier to forward trace a toll-free or DID number to a criminal than it is to trace a spoofed call from a criminal. This is because there are fewer phone companies involved and more accurate records are kept for longer periods of time.
Usually, a tech support fraud victim only calls the initial toll-free or DID number listed on a computer pop-up or e-mail once. After that, criminals will call identified potential victims using other DID numbers provided by services like Skype, Google Voice, Vonage, TextNow, TextFree, or Magic Jack. To avoid detection by phone companies, they will use unique DID numbers for individuals or small groups of victims. Providers of these DID numbers will also have records of the IP addresses used to receive calls.
Some criminal groups specialize in hybrid tech support and law enforcement impersonation scams where they will spend extended periods of time socially isolating potential victims before convincing victims to transfer funds.
When law enforcement investigates US-based IP addresses, in many cases they may be static premises IP addresses for which internet service providers will have a record of the location where they are used. In other cases, they may be remote servers or public WiFi hotspots. Additional investigation is needed for such non-premises IPs.
Additional steps may sometimes be needed to investigate Indian IP addresses. In some cases, a single premises IP addresses provided at a particular building in India may be used by multiple building occupants. In other cases, Indian “fixed wireless” providers may assign an IP address to a WiFi router on a telephone pole for use by multiple customers in an area.
However, given that tech support fraud groups in India have to contact a lot of potential victims, it is very difficult for such criminal groups to completely obscure their locations.
Implications for Policy Makers
A small number of US Federal Agents dedicated to identifying and calling phone numbers used for tech support fraud can effectively deter most or all of the $1 billion per year lost to India-based call center fraud.
- Such US Investigators can identify live tech support phone numbers through public records or police reports
- Investigators can call these numbers and record attempts to commit fraud.
- IP addresses used to receive calls can be obtained from phone service providers.
- Indian IP addresses can be provided to Indian police via Foreign Dissemination Reports.
This type of real-time monitoring, even at small scale, will deter tech support fraud because scam call centers will have no idea which calls are from victims and which are law enforcement investigations that will result in raids by Indian police.
As noted above, the FBI’s 2022 Internet Crime Complaint Center (IC3) annual report describes its efforts to deter tech support and call center fraud by cooperating with Indian police to effect successful prosecutions in Indian courts. These efforts should be lauded, encouraged, and expanded.
Traditional FBI investigations into fraud conspiracies take 2-3 years to complete and usually involve exhausting all avenues to identify all parties involved. If FBI is sending 2-3 case referrals to Indian police per year, it will have minimal impact on reducing the impact of fraud on Americans. If FBI focuses on sending Indian police Foreign Dissemination Reports identifying the potential locations of call center fraud 2-3 times per week, it will have significantly more impact on driving deterrence. FBI can continue to build larger cases by collaborating with Indian police and using evidence seized by Indian police during raids.